-
Lukáš Krupčík authoredLukáš Krupčík authored
- Obtaining Login Credentials
- Obtaining Authorization
- Authorization of PI by Allocation Committee
- Authorization by web
- Authorization by e-mail (an alternative approach)
- The Login Credentials
- Change Passphrase
- Change Password
- The Certificates for Digital Signatures
- Alternative Way to Personal Certificate
- Installation of the Certificate Into Your Mail Client
- End of User Account Lifecycle
Obtaining Login Credentials
Obtaining Authorization
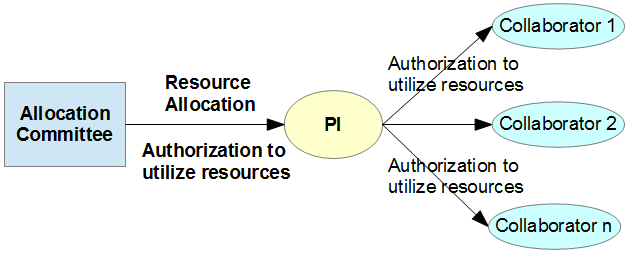
The computational resources of IT4I are allocated by the Allocation Committee to a Project, investigated by a Primary Investigator. By allocating the computational resources, the Allocation Committee is authorizing the PI to access and use the clusters. The PI may decide to authorize a number of her/his Collaborators to access and use the clusters, to consume the resources allocated to her/his Project. These collaborators will be associated to the Project. The Figure below is depicting the authorization chain:
!!! note You need to either become the PI or be named as a collaborator by a PI in order to access and use the clusters.
Head of Supercomputing Services acts as a PI of a project DD-13-5. Joining this project, you may access and explore the clusters, use software, development environment and computers via the qexp and qfree queues. You may use these resources for own education/research, no paperwork is required. All IT4I employees may contact the Head of Supercomputing Services in order to obtain free access to the clusters.
Authorization of PI by Allocation Committee
The PI is authorized to use the clusters by the allocation decision issued by the Allocation Committee.The PI will be informed by IT4I about the Allocation Committee decision.
Authorization by web
!!! warning Only for those who already have their IT4I HPC account. This is a preferred way of granting access to project resources. Please, use this method whenever it's possible.
This is a preferred way of granting access to project resources. Please, use this method whenever it's possible.
Log in to the IT4I Extranet portal using IT4I credentials and go to the Projects section.
- Users: Please, submit your requests for becoming a project member.
- Primary Investigators: Please, approve or deny users' requests in the same section.
Authorization by e-mail (an alternative approach)
In order to authorize a Collaborator to utilize the allocated resources, the PI should contact the IT4I support (E-mail: support[at]it4i.cz) and provide following information:
- Identify your project by project ID
- Provide list of people, including himself, who are authorized to use the resources allocated to the project. The list must include full name, e-mail and affiliation. Provide usernames as well, if collaborator login access already exists on the IT4I systems.
- Include "Authorization to IT4Innovations" into the subject line.
Example (except the subject line which must be in English, you may use Czech or Slovak language for communication with us):
Subject: Authorization to IT4Innovations
Dear support,
Please include my collaborators to project OPEN-0-0.
John Smith, john.smith@myemail.com, Department of Chemistry, MIT, US
Jonas Johansson, jjohansson@otheremail.se, Department of Physics, Royal Institute of Technology, Sweden
Luisa Fibonacci, lf@emailitalia.it, Department of Mathematics, National Research Council, Italy
Thank you,
PI
(Digitally signed)Should the above information be provided by e-mail, the e-mail must be digitally signed. Read more on digital signatures below.
The Login Credentials
Once authorized by PI, every person (PI or Collaborator) wishing to access the clusters, should contact the IT4I support (E-mail: support[at]it4i.cz) providing following information:
- Project ID
- Full name and affiliation
- Statement that you have read and accepted the Acceptable use policy document (AUP).
- Attach the AUP file.
- Your preferred username, max 8 characters long. The preferred username must associate your surname and name or be otherwise derived from it. Only alphanumeric sequences, dash and underscore signs are allowed.
- In case you choose Alternative way to personal certificate, a scan of photo ID (personal ID or passport or driver license) is required
Example (except the subject line which must be in English, you may use Czech or Slovak language for communication with us):
Subject: Access to IT4Innovations
Dear support,
Please open the user account for me and attach the account to OPEN-0-0
Name and affiliation: John Smith, john.smith@myemail.com, Department of Chemistry, MIT, US
I have read and accept the Acceptable use policy document (attached)
Preferred username: johnsm
Thank you,
John Smith
(Digitally signed)Should the above information be provided by e-mail, the e-mail must be digitally signed. To sign an e-mail, you need digital certificate. Read more on digital signatures below.
Digital signature allows us to confirm your identity in remote electronic communication and provides an encrypted channel to exchange sensitive information such as login credentials. After receiving your signed e-mail with the requested information, we will send you your login credentials (user name, key, passphrase and password) to access the IT4I systems.
We accept certificates issued by any widely respected certification authority.
For various reasons we do not accept PGP keys.** Please, use only X.509 PKI certificates for communication with us.**
You will receive your personal login credentials by protected e-mail. The login credentials include:
- username
- ssh private key and private key passphrase
- system password
The clusters are accessed by the private key and username. Username and password is used for login to the information systems.
Change Passphrase
On Linux, use
local $ ssh-keygen -f id_rsa -pOn Windows, use PuTTY Key Generator.
Change Password
Change password in your user profile.
The Certificates for Digital Signatures
We accept personal certificates issued by any widely respected certification authority (CA). This includes certificates by CAs organized in International Grid Trust Federation, its European branch EUGridPMA and its member organizations, e.g. the CESNET certification authority. The Czech "Qualified certificate" (Kvalifikovaný certifikát) provided by PostSignum or I.CA, that is used in electronic contact with Czech authorities is accepted as well.
Certificate generation process is well-described here:
A FAQ about certificates can be found here: Certificates FAQ.
Alternative Way to Personal Certificate
Follow these steps only if you can not obtain your certificate in a standard way. In case you choose this procedure, please attach a scan of photo ID (personal ID or passport or drivers license) when applying for login credentials.
- Go to CAcert.
- If there's a security warning, just acknowledge it.
- Click Join.
- Fill in the form and submit it by the Next button.
- Type in the e-mail address which you use for communication with us.
- Don't forget your chosen Pass Phrase.
- You will receive an e-mail verification link. Follow it.
- After verifying, go to the CAcert's homepage and login using Password Login.
- Go to Client Certificates -> New.
- Tick Add for your e-mail address and click the Next button.
- Click the Create Certificate Request button.
- You'll be redirected to a page from where you can download/install your certificate.
- Simultaneously you'll get an e-mail with a link to the certificate.
Installation of the Certificate Into Your Mail Client
The procedure is similar to the following guides:
MS Outlook 2010
Mozilla Thudnerbird
End of User Account Lifecycle
User accounts are supported by membership in active Project(s) or by affiliation to IT4Innovations. User accounts, that loose the support (meaning, are not attached to an active project and are not affiliated with IT4I), will be deleted 1 year after the last project to which they were attached expires.
User will get 3 automatically generated warning e-mail messages of the pending removal:.
- First message will be sent 3 months before the removal
- Second message will be sent 1 month before the removal
- Third message will be sent 1 week before the removal.
The messages will inform about the projected removal date and will challenge the user to migrate her/his data